Keycloak¶
Open Source Identity and Access Management
Homepage: https://keycloak.org - Version: 18.0.0
Installation¶
Docker¶
docker-compose, example¶
- to be run behind https-enabled reverse proxy (Traefik)
auth:
image: quay.io/keycloak/keycloak:18.0.0
command: start --auto-build
environment:
KC_DB: mssql
KC_DB_URL_HOST: db
KC_DB_URL_DATABASE: keycloak
KC_DB_USERNAME: ${MSSQL_DB_USER}
KC_DB_PASSWORD: ${MSSQL_DB_PASS}
KC_TRANSACTION_XA_ENABLED: false
KC_PROXY: passthrough
KC_HTTP_ENABLED: "true"
KC_HOSTNAME_STRICT: "false"
KEYCLOAK_ADMIN: admin
KEYCLOAK_ADMIN_PASSWORD: secret
Windows¶
- Download Keycloak Server (Distribution powered by Quarkus) and unzip
- configure database in conf/keycloak.conf
- run bin/kc.bat start --auto-build
-
if run is successful then install as a service:
X:\GiS\Insight\Keycloak\bin\keycloak-service.bat install
-
Configure the newly created "Keycloak" service from
manualtoautomatic - Start the service
Configuration / Realm¶
additional documentation https://www.keycloak.org/docs/latest/server_admin/
- open Keycloak Admin Console
-
http://localhost:8080
-
create admin-user
- add new realm
-
-
import
insight-realm.jsonwhile creating a new realm 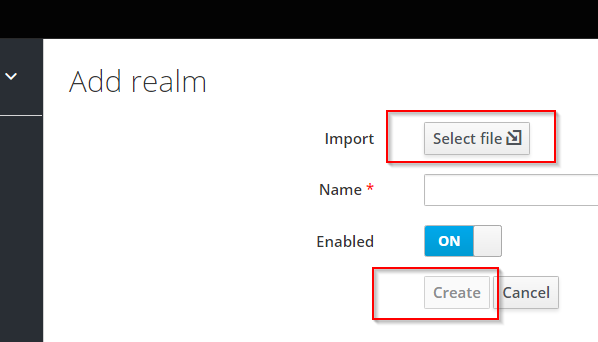
- regenerate
secretforinsight-apiclient 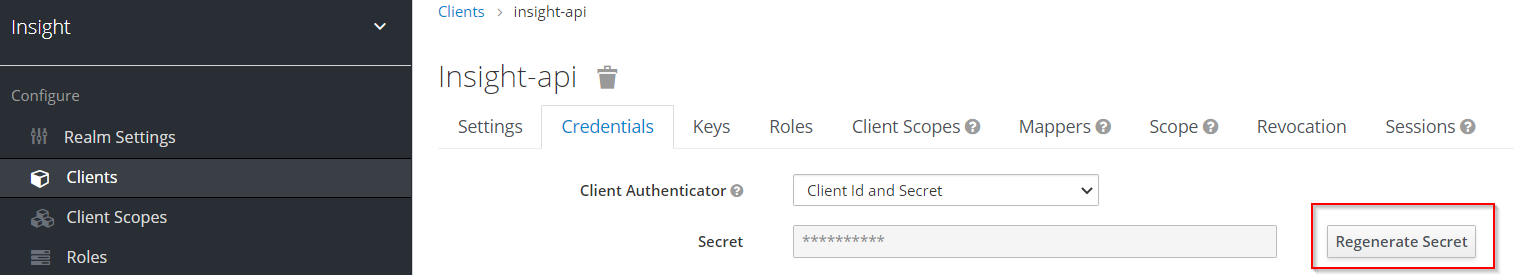
- Copy secret-value and set
oidc.techuser.client_secretin insight.properties - fix URLs for clients:
insight-app&insight-cockpit -
replace
external.hostname.tldwith the external hostname of your Insight server -
create a new (technical/system) user to be configured in the middleware
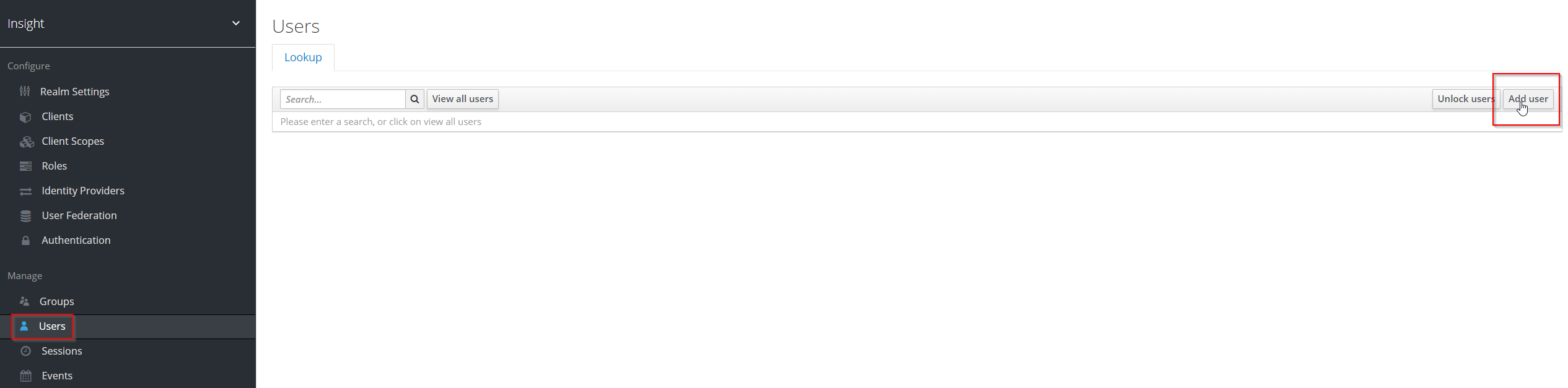
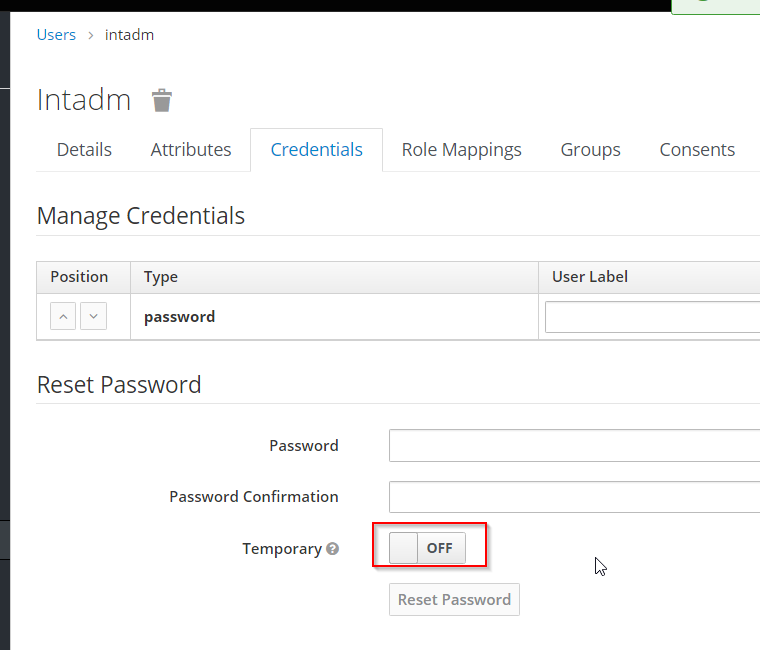
- Switch "Temporary" to "off" otherwise passwort is only valid till next login and user is forced to change password
- set values into
oidc.techuser.usernameandoidc.techuser.passwordin insight.properties
Continue with OIDC-Integration